- Finally, budget wireless earbuds that I wouldn't mind putting my AirPods away for
- I replaced my Linux system with this $200 Windows mini PC - and it left me impressed
- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
Private 5G Security Risks in Manufacturing Part 4

Exploits & Vulnerabilities
We can see signs of increased activity in areas of business that use 5G around the world. 5G technology will usher in new personal services through smartphones, and it will also play a large part in industry.
Read time: ( words)
The option of Private 5G lets private companies and local governments have their own telecom infrastructures. However, the “democratization of communications” entails its own risks that have not yet been made clear. To identify these risks, Trend Micro performed tests using an environment modeled after a steelworks with 5G equipment. In this fourth and final installment, we discuss the essential security measures for user companies with Private 5G infrastructure.
In the previous article, we looked at the potential penetration routes that arise when migrating to an open Private 5G system. We also discussed the possibility for an attacker to physically damage a manufacturing site by infiltrating the user plane that deals with user data and then performing a man-in-the-middle attack. In light of this, system administrators and security officers should take action at their organizations to address the security risks in CT (Communication Technology) identified in this test, on top of conventional IT and OT security.
Looking at things from the attacker’s perspective
When thinking about defense, it is vital to think from the attacker’s perspective. In other words, effective measures can be designed by understanding why an attacker would make the effort of targeting the core network. As we have discussed earlier, the core network is the foundation that handles information and that has a direct impact on the confidentiality, integrity, and availability of manufacturing processes (Fig. 1). As such, this system provides many attack options for malicious actors, such as stealing information or causing damage.
Private 5G and other forms of network infrastructure cannot be easily changed or renewed once they are built and start running. This foundation is appealing to attackers as it lets them secretly infiltrate deep into their network of choice and they are afforded a lot of time to accomplish their final goal. Attackers are ready to expend significant resources to breach this system, so companies can face extremely critical damage if they are targeted. As such, if a user company is looking to implement a Private 5G configuration, it is effective to take an approach based on Security by Design and prepare security measures with a medium- to long-term perspective that anticipates an attacker infiltrating the system. Specifically, we recommend the following three actions:
- Enforcing encryption and authentication/permissions in the core network
- Verifying security at the PoC phase
- Building a structure to detect abnormalities swiftly
Three elements for realizing Security by Design in Private 5G
- Enforcing encryption and authentication/permissions in the core network
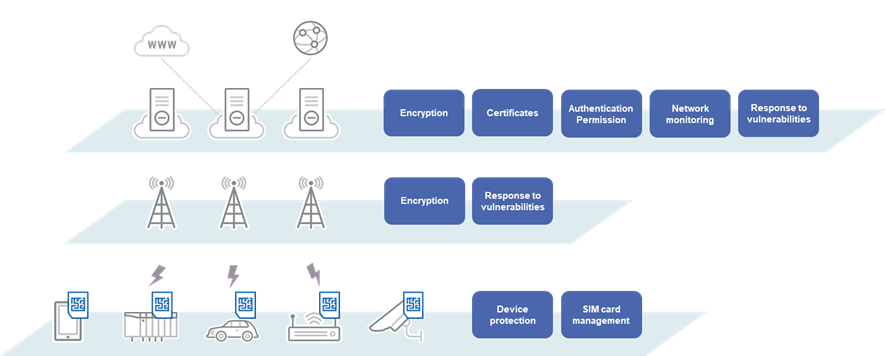
Our research showed that the core network is a new area for potential attack, thereby presenting a security risk in implementing Private 5G. The core network is essential for building a mobile communication system, as well as a crucial component in handling user data. To secure the core network, it helps to first understand the areas that attackers can exploit. Our test revealed four penetration routes and three signal interception points, and we identified six scenarios of how attackers can exploit these weaknesses.
| Name | Potential damage | Technological strategies to mitigate risk | |
| 1 | MQTT hijacking | Damage to products Impairment of the manufacturing process |
Use usernames, passwords, and certificate pinning and implement MQTTS (encrypted MQTT). |
| 2 | Modbus/TCP hijacking | Damage to products Impairment of the manufacturing process |
Set up a VPN between the remote site and the control network. |
| 3 | PLC firmware reset | Damage to products Impairment of the manufacturing process |
Set up a VPN between the remote site and the control network. Configure “Read/Write” protection when installing the PLC. Install new firmware that supports challenge–response authentication. |
| 4 | DNS hijacking | Theft of confidential information Contamination of equipment with malware |
Install an EDR or network monitoring tool that can detect suspicious IP addresses. Use an industrial protocol that supports encryption and certificate pinning. |
| 5 | Remote desktop exploits | Theft of confidential information Lateral movement through privilege escalation |
VNC: Enable TLS encryption and certificate pinning. Enable client authentication. Microsoft RDP: Use version 10 or higher. |
| 6 | SIM swapping | Theft of confidential information Lateral movement |
Bind devices to specific SIM cards. Trend Micro Mobile Network Security (TMMNS) from Trend Micro can mitigate this risk. |
<Table 1> Attack methods identified in our research, and technological strategies to mitigate them
Except for SIM swapping, all these attacks start with the interception of signals in the core network. Effective technological strategies to combat these attacks mainly involve encrypting communications and managing authentication and permissions, including SIM cards. In more detailed terms, this involves using a protocol that supports encryption, installing EDR, XDR, or other detection and response tools, and managing SIM cards so that they are associated with devices. These are all crucial elements for a Zero Trust configuration, so it can be considered vital to think about Zero Trust when designing the core network in a Private 5G environment. Of course, the encryption features can be breached by attackers if the system has inherent vulnerabilities, so it is still important to address any weak points in the system.
- Verifying security at the PoC phase
User organizations looking to implement Private 5G need to first clarify their security requirements at the design stage, and they need to do this while working closely with their system integrator as a partner. We can expect to see more and forward more companies building PoCs with a view to implementing a full-scale Private 5G configuration going forward. However, it is unfortunately rare for security requirements to be verified at the PoC phase.
A Private 5G network is the foundation for accelerating IoT deployment. Just like how you wouldn’t change a building’s foundations after it’s been built, you will get better results by using built-in security rather than resorting to add-on security. For this reason, we recommend incorporating the areas of risk identified in this research as areas for consideration in the PoC (Fig. 2). It is possible to significantly mitigate risk by addressing penetration routes and interception points confirmed this time at the design stage.
- Building a structure to detect abnormalities swiftly
As cyber attacks grow more complex and refined, it is increasingly crucial to carry out measures to mitigate these internally. Company network borders are becoming more vague and complicated with the accelerated pace of digital transformation. Malicious agents will use every possible attack route to try to infiltrate the system and reach the resources within the network. Factories and other production sites are valuable resources in the eyes of attackers (Fig. 3). This year, a major U.S. oil pipeline company called Colonial Pipeline was hit by a cyber attack, resulting in its business being halted for five days. According to reports, the company’s IT system got attacked, and so they shut down the control system to prevent the damage spreading further. This action resulted in the suspension of business activities.
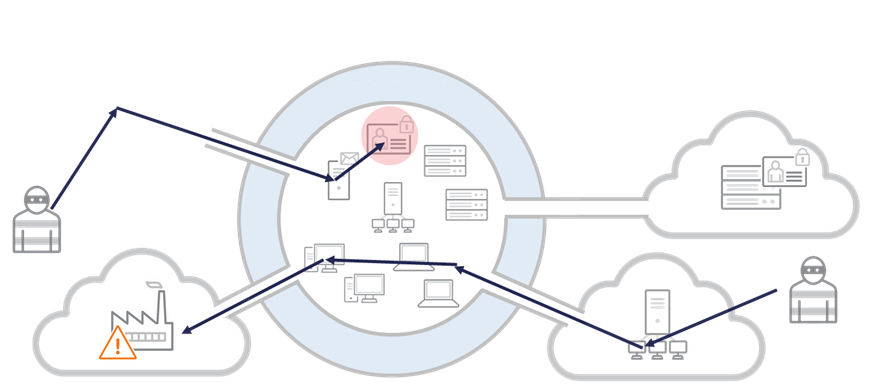
In this way, cyber attacks on control systems often operate via IT.
If it is not possible to see the current state of the system or the possible threats, you cannot predict the extent of damage following an attack. Many manufacturing companies face the same kinds of issues. As systems grow more and more complex, cyber attacks also feature increasingly complicated approaches. To fight these attacks, it is vital to have functionality that constantly monitors the whole system and swiftly detects any changes.
As such, implementing XDR over multiple layers including IT, OT, and CT can significantly help mitigate business risk. Trend Micro offers effective solutions that can be implemented in this area.
This covers our recommended security measures based on our research.
Through the four parts of this series, we have discussed the potential cybersecurity risks that can arise when implementing a Private 5G system in manufacturing as well as actions that can be taken to mitigate these risks based on a field test held by Trend Micro. We hope that our research can help user organizations looking to implement Private 5G.

YOHEI ISHIHARA
Security Evangelist,
Global IoT Marketing Office,
Trend Micro Incorporated
Graduated from the Department of Criminology, California State University, Fresno. Joined Trend Micro after experience with sales and marketing at a hardware manufacturer in Taiwan, and SIer in Japan. Collaborates with researchers worldwide to collect and provide threat information, with a focus on factory security, 5G, and connected cars. Works as a Security Evangelist to think about cyber risks in light of social conditions, and to raise awareness about security issues as a form of geopolitical risk.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

